Article
QRadar: Security analytics at speed
With advances in technology and the reoccurrence of data leaks, cyber security is a more significant challenge than ever before. Cyber attacks evolve as quickly as the technology itself, and hackers are finding more innovative ways to break security controls to access confidential data and interrupt services. Hackers reinvent themselves using new technology features as a tool to expose companies and individuals. Therefore, cyber security cannot be reactive but must go a step further by implementing proactive security controls that protect the most important assets of every organization: the company’s information.
In cyber security, Security Information and Event Management (SIEM) can be considered a series of technologies that provide analysis, threat mitigation, and logging of security events across a network. SIEM provides a general view of all technical infrastructure, with specific data of security events, and the mitigation of those infrastructures. SIEM includes functions, such as Security Information Management (SIM) and Security Event Management (SEM), into a single solution.
Beyond threat detection and response, QRadar SIEM enables security teams to proactively manage threats with advanced AI, powerful threat intelligence, and access to cutting-edge content to maximize analyst potential. Whether you need cloud-native architecture built for hybrid scale and speed or a solution to complement your on-premises infrastructure, Covenco and IBM can provide you with a SIEM to meet your needs.
To better understand SIEM, IT Managers need to consider it as a solution that gathers data from security sources for analysis correlation and action upon possible threats. SIEM management offers a variety of functions in the following areas:
- Event and log collection
- Rule correlation
- Log source management
- Adaptability
- Data normalisation and registry
IBM Qradar can solve scenarios where people cannot analyse advanced threats using the standard monitoring tools, on a general level, by using a business technical infrastructure and by unifying all the elements, which are typically agents in a hierarchical model, to gather events from endpoints, servers, and network equipment. It provides third-party interoperability so that many solutions can be integrated, which makes this product scalable and more robust.
QRadar is an IBM Security prime product available from Covenco, designed to be integrated with corporate network devices to keep real-time monitoring of security events through a centralised console.
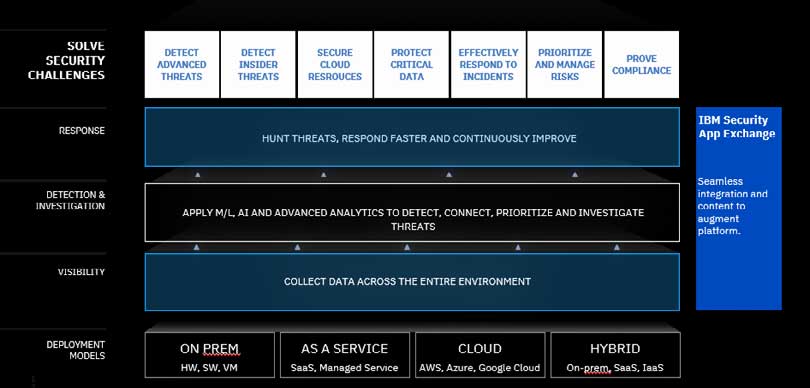
Why IBM QRadar for SIEM
QRadar is one of the most popular SIEM solutions for enterprise data management and security. It is a network management platform that provides situational awareness, event management, and data recollection into a central console. This console normalises the data, correlates signatures, events, and flows, and analyses traffic for any potential threat within a technical environment.
QRadar combines flow-based network knowledge, event correlation, and asset-based vulnerability assessment.
Maximize analyst time and talent
Experience the power of IBM enterprise-grade AI designed to amplify the efficiency and expertise of every security team. With QRadar SIEM, analysts can reduce repetitive manual tasks like case creation and risk prioritization to focus on critical investigation and remediation efforts.
Accelerate Threat Detection and Response
Disrupt advanced cyber-attacks and respond faster with cutting-edge content, including native Open Source SIGMA community integration. No additional context needed with correlated log event data including IBM X-Force Threat Intelligence, user behavior analytics, and network analytics.
Reduce security complexity
Easily work across all data source types and security tools with robust interoperability. Equipped with over 700 pre-built integrations and partner extensions, QRadar SIEM seamlessly integrates with your existing threat detection tools to ensure you get complete visibility across your security ecosystem.
Use Cases
Advanced threat detection
Responding to advanced threats is resource intensive, time consuming and time sensitive. Accelerate detection with visibility and AI.
Threat hunting
Generate comprehensive intelligence and help your analysts hunt for cyberthreats in near real time by turning disparate data sets into action.
Ransomware
Fast ransomware attacks demand faster responses. With attackers moving faster, organizations must take a proactive, threat-driven approach to cybersecurity.
Compliance
Show evidence of compliance and declaration of conformity with applicable regulatory statutes and internal audits for your environment.
QRadar architecture
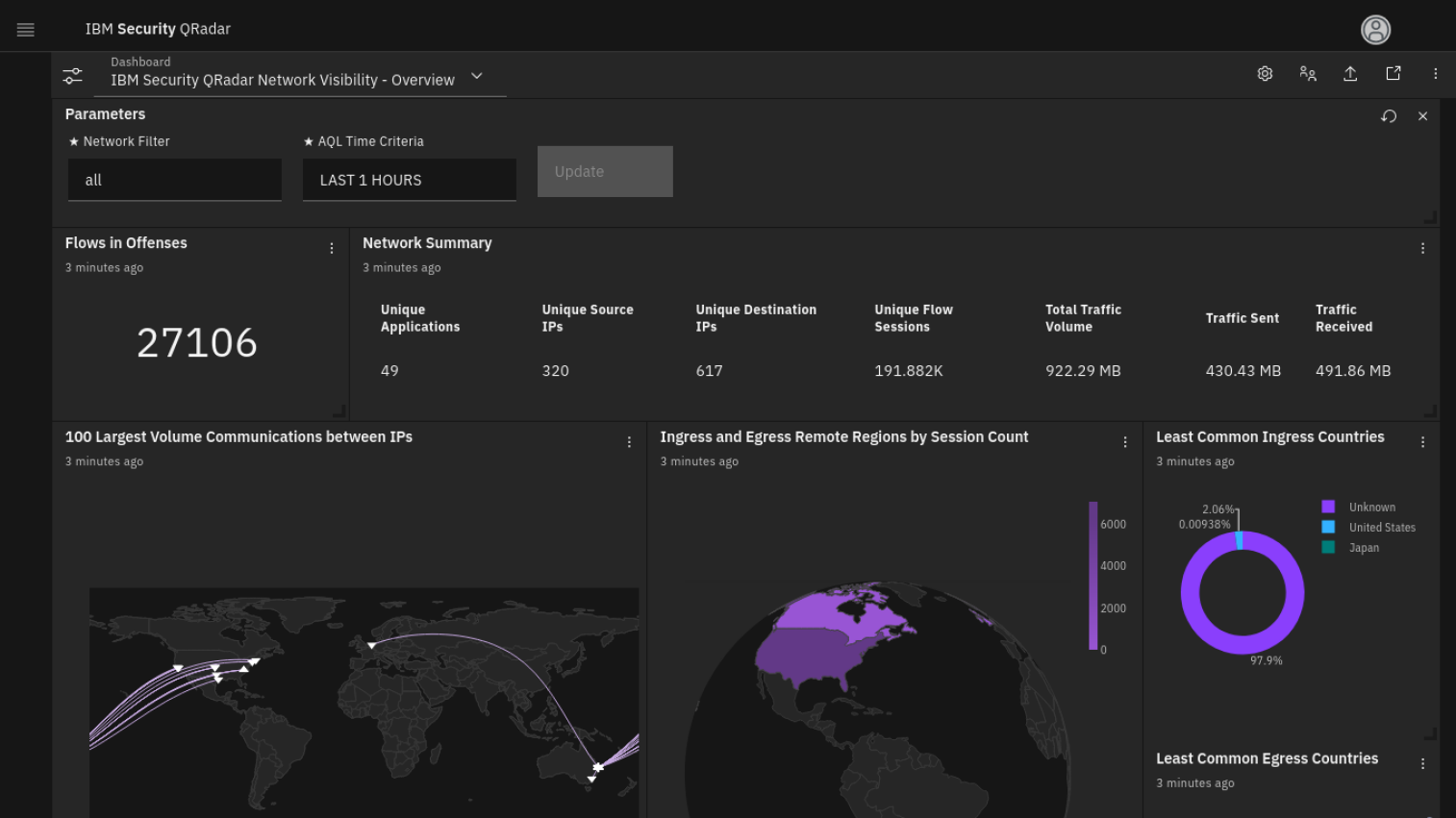
The IBM Security QRadar system collects, processes, aggregates, and stores network data in real-time. It uses that data to contribute to your network security by providing real-time information and correlation; the system correlates all network security events and flows and generates alerts and offences that your network security team can analyse.
A word about QRadar high availability
As with other information technology and security systems, ensuring they are always available is essential. In the case of a security system as crucial as the IBM Security QRadar system, it is always a good practice to include a high availability (HA) setup or solution to ensure the system is always available to reinforce the security of the network infrastructure.
Having a QRadar HA solution, the system can continue to collect, store, and process event and flow data even if there is a hardware or software failure. To get the system working on a HA environment, QRadar connects a primary HA host with a secondary HA host and configure a virtual IP (VIP) to create an HA cluster.
The concept around HA is similar to other HA deployments found with other vendors. You install and configure a second appliance that takes over the primary role in case a failure on the primary occurs. The secondary HA host maintains access to the same data as the primary host using data synchronization or shared external storage. It also inherits the license from the primary HA host so that there is no need to purchase and apply a separate license for the secondary host.
Some of the failures that can potentially affect the operation of the primary systems are failures on a power supply, a network failure detected by the network connectivity tests. This operating system failure delays or stops the heartbeat ping tests, a complete RAID failure, and a failure on the management interface. It might also be possible to trigger a manual failover for the secondary system to become the primary one.
For a more in depth review of QRadar from IBM, and how you can achieve a comprehensive SIEM solution for your organisation, speak to the IBM Team at Covenco today. We can offer pre-sales engineering, design and consultancy alongside your hardware and data management projects.

